Organizations must mitigate their cloud security risks based on the type of cloud they have.
- Gartner client? Log in for personalized search results.
Cloud Security — Understand, Mitigate and Manage Risk Types
Evaluate cloud security controls using outcome-driven metrics
As the use of cloud services continues to grow worldwide, a shift in security approaches and technologies is underway. Security and risk management leaders need a different spending model backed by business-relevant metrics.
Use this research to:
Balance cloud security investments with business-relevant outcomes.
Define outcome-driven metrics to assess cybersecurity results.
Ensure your investment reflects the level of protection it achieves.
Understand and mitigate cloud security risks
Cloud computing has many advantages, such as sharing storage and resources, but can also lead to cloud security risks. Learn how to manage those risks to protect data and intellectual property.
- Is the Cloud Secure?
- Cloud Security Risks
- Risks by Type & Model
- Mitigating Cloud Risks
Public cloud security breaches are very rare
Cloud use does not result in higher security or continuity failure. It appears to be the opposite. Customer error accounts for most breaches. Properly used, cloud computing is safe and secure.
The strong security delivered by cloud service providers (CSPs) is due to:
Scale — Delivering service to multiple organizations enables cloud providers to invest in resilience and security.
The ability to dynamically allocate resources — Cloud providers can deliver encryption, authentication and filtering across their services.
Competition between vendors — Strong security is a differentiator for providers within a competitive market.
Standardization of security processes — As providers mature and obtain certifications such as ISO27001, client organizations can potentially replace legacy security technologies without incurring capital expense.
Fewer than 20 globally active CSPs provide the majority of worldwide cloud processing. “Tier 1” CSPs are characterized by over a decade of reliable service and market dominance. When it comes to security, they provide world-class levels.
Second- and third-tier CSPs are somewhat riskier, as evidenced by several data leaks and ransomware incidents that have affected customer organizations in recent years.
That is not to say that there are no risks to using the cloud. Rather, these risks are not limited to cloud security. Many are connected with relinquishing control over governance and compliance. In order of impact, the top risks include:
Wasted employee time
Overspend
Agility risk/technology debt
Slow time and downtime
Security exposure and data leakage
Compliance and audit complications
Program risk
To start assessing cloud security, organizations should look at the following factors:
Internal or external — The physical location of your organization’s data.
Proprietary or open — The ownership of the cloud technology, services and interfaces and the degree of interoperability and transportability between them.
Perimeterized or deperimeterized — Whether security protections are in place at the data level or through a traditional, infrastructure-based perimeter.
Insourced or outsourced — Whether a third party or your own staff deliver cloud services.
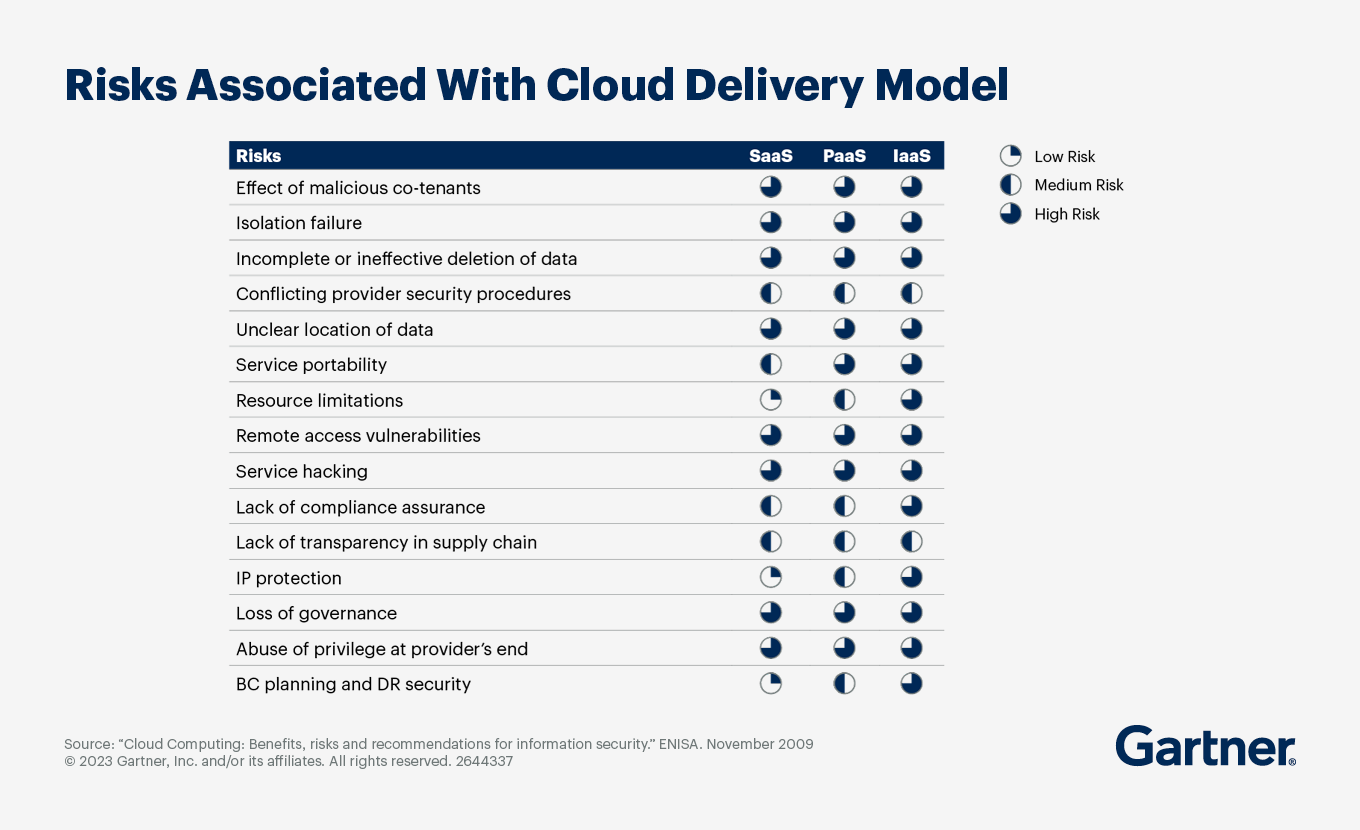
Common cloud security risks relate to resource sharing and data protection
The biggest security risks in the cloud include those that are unique to cloud computing — involving resource sharing and remote access to data — and third-party risks.
Shared resource and remote access risks
The shared resource model increases exposure to three key risks:
Malicious co-tenants sharing the same computing resources could potentially affect a customer’s access to the resources, leading to data and reputation loss.
Isolation failure occurs when the provider fails to separate memory, routing and storage among the tenants of a shared resource model. This can make organizations vulnerable to attacks targeted at other tenants.
Ineffective deletion of data can occur when the service provider fails to properly remove data that adds no business value or has outlived its usefulness (separate from the business units being unwilling to part with data, a common problem that is not unique to the cloud).
Third-party risks
Some third-party risks are cloud specific. They include:
Conflicting security procedures — When the provider and the customer have conflicting security controls, it can create problems with daily operations.
Service portability — Technical feasibility and cost concerns regarding portability are a source of risk in part due to the absence of regulatory standards for cloud computing.
In addition to cloud-related security risks, organizations should also account for traditional third-party risks that affect outsourced data, such as:
Resource limitations — Inaccurate modeling and planning by the provider can result in inadequate resource provision, thereby resulting in higher likelihood of service unavailability or compromised quality.
Remote access vulnerabilities — Remote access of data increases the likelihood of attack during transmission between the cloud and the host’s systems.
Service hacking — Hacking by malicious parties puts a lot at stake in the cloud.
Lack of compliance assurance — Cloud service providers may not meet all industry standards and security requirements, a risk that increases if the provider doesn’t permit auditing.
Lack of transparency in the cloud supply chain — If the provider outsources specialized aspects of its service to a third-party provider, any interruption in this chain of services can have a direct impact.
Intellectual property (IP) protection — In models such as PaaS and IaaS, the provider and organization must take adequate measures to protect IP of new products created over a publicly shared interface.
Loss of governance — No provision is in place to check if data resides at the service provider or at a third party, or if these providers are compliant. This can negatively affect data confidentiality and integrity assurance.
Abuse of privilege at provider’s end — Highly technical roles at the cloud provider can have access to sensitive customer information, which they could misuse without the user organization knowing.
Business continuity (BC) planning and disaster recovery (DR) — Providers are responsible for the data within the cloud and therefore must have their own BC and DR plans in place. Lack of transparency about them can hamper BC and DR strategies.
Cloud security approaches should vary by cloud type and delivery model
There are three types of cloud delivery models, each with slight differences in the main risks that affect them.
Software as a service (SaaS) involves an external entity owning, hosting and managing a software application and delivering it as a service to the end customer. Salesforce and Google Docs are SaaS examples. The SaaS customer is a specific end user using it to fulfill business functionality requirements.
Platform as a service (PaaS) is a software development platform available as a service that supports the end-to-end software development life cycle, including design, testing and deployment. Examples include Microsoft Azure and Google App Engine. The target market for PaaS is software developers and independent software vendors.
Infrastructure as a service IaaS is a service-based model for provisioning core computing power servers, storage and network resources for deployment and execution of externally hosted applications. Examples of IaaS include Amazon EC2 and Oracle Coherence. The target market for IaaS is architects, infrastructure groups and network or system administrators.
Many sources of cloud security risk are equally high (or low) across SaaS, PaaS and IaaS cloud types. Nonetheless, IaaS has the highest level of risk associated with it, specifically for the following sources: service portability, resource limitations, lack of compliance assurance, IP protection and business continuity planning and disaster recovery security.
Whether these models are deployed on a public, private or a hybrid cloud also affects its cloud security.
Public clouds make resources available dynamically over the internet from third-party source providers. This is the most commonly understood form of cloud computing.
Private clouds make advanced use of virtualization inside the enterprise to emulate cloud computing benefits on an internal infrastructure.
Hybrid clouds combine the features of public and private cloud models, allowing for data and application portability between multiple clouds.
Security risks are much higher in a public cloud, where organizations have to rely on the provider for security. Most risks don’t apply to private deployment models. Those that do include service portability, resource limitations and remote access vulnerabilities and service hacking.
Enforce more effective and transparent contracts to reduce risks
Reduce cloud security risk by defining the provider’s security responsibilities and then monitoring the service performance:
Involve security throughout the deal’s life cycle. This helps clarify the division of responsibilities and ensures security requirements become a contractual obligation.
Use encryption to protect data in the cloud. Encrypting data during transmission and at rest can help prevent accidental disclosure and incomplete deletion of data.
Develop a strong auditing approach:
Continually assess security capabilities through regular audits to ensure consistent maintenance of security controls.
Audit logs, activity reports, system configuration and change management reports to monitor service performance.
Select auditors who are familiar with cloud technologies to make the auditing process more efficient.
Partner with the provider to leverage their security expertise. Having a clear discussion with the cloud provider on how they handle data at their end can help organizations modify information security policies or create new ones.
Ensure security certifications at the provider’s end. There are no standards specific to security in the cloud, yet it helps to check the provider’s preparedness to meet security standards such as ISO 27001 and ISO 27002 for security management, which measure the provider’s quality of security.
Make sure the provider insures against data breaches. Insist on insurance from the provider to make sure that you can recover damages.
Experience IT Security and Risk Management conferences
Join your peers for the unveiling of the latest insights at Gartner conferences.