Organizations constantly face new cybersecurity threats, but the ones most likely to create problems are familiar.
- Gartner client? Log in for personalized search results.
Cybersecurity Threats: How to Prioritize, Manage and Reduce Them
Three ways to move beyond managing cyber risk in isolation from the business
Lack of resources, siloed operations and poor tool implementation often prevent security and risk management (SRM) teams from detecting and responding to threats. Yet taking a risk-based approach can help improve efficiency in threat detection and increase your response time.
This research helps SRM teams:
- Break down silos between SRM and business leaders
- Enrich information and processes to save time and ensure successful execution
- Prioritize for faster incident response
Stay effective against the most likely cyberthreats
Continuous technology changes driven by DX create an expanded attack surface that malicious actors can exploit. Protecting digital assets requires CISOs to monitor and respond to these changes.
- Prioritize Threats
- Top Threats
- High-Momentum Threats
- Uncertain Threats
- From Threats to CTEM
Identify the highest impact cybersecurity threats to focus your resources
Addressing every potential threat has always been operationally infeasible. More so now, given the way digital transformation, cloud computing, hybrid work and other trends have expanded the attack surface (see also the From threats to CTEM tab). SRM leaders must focus their activity and resources on the most likely and impactful cybersecurity threats and threat exposures. These fall into the following three categories:
- Top threats. Threats that organizations are highly aware of and remain relevant year after year as a result of changing tactics.
- High-momentum threats. Threats that are growing, but for which awareness is lower than with the top threats.
- Uncertain threats. “Low signal” threats, which may be emerging and dangerous, or overhyped and a distraction — it’s up to the organization to determine which.
Several factors guide security leaders in determining whether to invest, or not, in responding to a specific threat, regardless of the category they fall into:
Relevance: Could the threat impact our operational continuity?
Urgency: Could the threat affect our ability to operate, and to what degree?
Maturity: Do we have an effective response plan in case the threat affects us?
Opportunity cost: Does the cost to address the threat outweigh the cost of the threat impact itself?
Measurability: Can we demonstrate to business leaders the value of investing in protecting ourselves?
Gather different types of information about past events to inform decisions about which threats scenarios to prioritize or deprioritize for the present and the future. Analyze stories, statistics and business changes to gain insights from the past. Then prepare for and arbitrate between trends in the threat landscape to make decisions on which controls to invest in, accelerate or divest for the present and the future.
The dynamic business environment should also influence which cybersecurity threats to prioritize. In addition, unknown inflection points can alter the threat landscape. Therefore, be sure to reserve some budget to address unpredicted threats.
Maintain focus on familiar threats that pose high risk due to micro-changes
For the last decade or so, the same compromise types have resulted in the highest impact with the greatest frequency. Specifically, malware, phishing and credential abuse. Rallying support from business stakeholders for these familiar threats may be difficult if they believe the risks have already been addressed. Security and risk management leaders should instead emphasize that even if the macro-threat is the same, the microtrends associated with them change. For example:
Malware/Ransomware
Ransomware as a service (RaaS) enables attackers to use existing ransomware tools to execute cyber extortion attacks. Government agencies continue to collaborate in an effort to take down some of the larger malware infrastructures, but attackers simply pivot to new approaches. For example, ransomware operators are shifting from relying solely on encryption to other forms of cyber extortion, including nonrecoverable data corruption, hardware corruption, data theft and data mining. Organizations are also seeing more risks with paying ransom and less protection from cyber insurance due to tighter standards.
Evolving phishing tactics
Phishing involves using multiple channels, predominantly email, but also collaboration platforms, social media, text messaging (smishing), voice messaging (vishing) and even quick response (QR) codes to gather information.
Successful phishing is frequently the first step that leads to additional impacts such as data exfiltration, credential theft, reputation and financial loss for an organization. Attackers continue to evolve their techniques with improved targeted content, automation and more realistic impersonation. Phishing continues to be a top contributor to data loss incidents. Approaches are getting more sophisticated using social engineering that is hard to detect.
Credential abuse
Credential abuse includes instances when an attacker is able to log in as an employee (or other person with legitimate access to an enterprise’s infrastructure, applications and data) or hijack an active session. In recent years, Verizon’s annual reports on data breaches show that stolen credentials are the most significant vector for these attacks. Many modern attacks have defeated multifactor authentication methods, though they remain a best practice method for stopping ATO, especially if they use modern authentication methods and flows.
Raise knowledge and awareness of high-momentum threats that have a low profile
High-momentum threats represent high risk to the organization, but there is generally less awareness about them unless your organization, or another in your industry, has been attacked.
Adapting to high-momentum threats requires security leaders to increase their knowledge of the business assets likely to be targeted. Two examples are APIs and cyber-physical systems (CPS). An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the organization’s security posture.
Examples of high-momentum threats include:
Customer account takeover
In customer account takeover (customer ATO), an attacker is able to log in as a customer of your services. Although applicable to any B2C service involving a customer login, this is most prevalent in financial services, digital commerce services that allow customers to store payment card details, cryptocurrency wallets and exchange accounts, and loyalty program accounts.
Social engineering continues to be a dominant attack method, although it has evolved beyond an attacker trying to obtain a victim’s credentials to authorized push payment (APP) fraud, whereby a victim sends money from their account under false pretenses. Security teams have difficulty detecting this because the victims themselves are logging on to their accounts. Brand impersonation carried out via websites, social media accounts or apps that imitate the genuine B2C brand is another method.
Cloud risks
The breadth and attack surface of cloud services continue to expand as cloud usage increases. The biggest danger remains customers misconfiguring their cloud environments. When attacks against cloud providers of any scale are successful or infrastructure outages occur, the consequences can be widespread. Yet this is rare. The use of cloud appears to present a security and availability advantage to most end users.
API abuse
API abuse refers to misuse of the APIs produced by an organization, either exploiting technical vulnerabilities or business logic. The attacker’s goal is to extract data. Attack techniques include API data scraping and account brute-forcing. Even if the more mature application security programs now include guidelines for protecting APIs, most corporations still have not taken action to address the scale and specificity of the API security challenge.
That challenge is evolving due to the fact that API traffic is increasing faster than most security teams can handle. In addition, APIs are becoming the main way of accessing enterprise data and application functionality.
Targeted attacks on cyber-physical systems (CPS)
Also referred to as Internet of Things (IoT), Industrial Internet of Things (IIoT), robots or smart systems, CPS are engineered to interact with the physical world. As they connect to each other and to enterprise systems, they greatly expand the attack surface, and present human safety and environmental risks.
State actors used to have a monopoly on deploying targeted attacks on CPS, but ransomware groups have become more aggressive even as they develop solutions to evade detection. In addition, the list of destructive malware specifically designed to target industrial CPS is growing and accelerating.
Decide if any uncertain threats represent a current source of risk
Uncertain threats are not supported by a strong fact base. They might be highly visible and recent, or older, but they are the most difficult problems to address, because they change year over year and are highly susceptible to excessive hype or uncertainty.
Uncertain threats fall into the following four categories:
Nascent. These threats belong to emerging architecture and technologies that do not exist in production environments. For most organizations, these threats represent no production risk.
Hyped. Hyped threats suddenly gain a lot of attention based on anecdotal evidence. They might present a risk, but the examples distract security leaders from the underlying and longer-term work. The ChatGPT-based attacks in the beginning of 2023 are good examples.
Emerging. Security teams lack strong prevention, detection and response capabilities for threats from new technologies the business has adopted.
Latent. Latent threats share the common attribute of being below the radar for most organizations, based on the assumption that attackers will exploit easier targets.
Examples of uncertain threats include:
Attackers using AI
Gartner defines AI as applying advanced analysis and logic-based techniques (including machine learning [ML]) to interpret events, automate decisions and take actions. Attackers can, and do, use AI techniques to improve their attacks by either shortening the time to achieve the strategic objective or to circumvent security controls. Examples of actual uses are limited, however, and the closest indications of effective uses of AI come from forums frequented by attackers.
Potential methods include: social engineering using video and audio content; phishing, in particular with AI-generated phishing emails; semiautomated malware creation to accelerate malware development and get better at avoiding detection; security control bypass, such as using ML to create malware variants or to defeat image recognition; and password hacks using machine learning techniques to crack passwords.
Attacks on AI
As AI models become more pervasive, attackers are advancing their techniques to manipulate AI outputs for their advantage. They are also finding new ways to steal personal and other sensitive data used to train AI models. Inputs that manipulate AI model outputs are another way to attack AI applications. Security controls are generally lacking or much weaker for AI model attack surfaces.
Nontechnology threats
Nontechnology cyberthreats involve digital assets over which businesses do not have automated control, such as the behavior of employees and identities related to third-party platforms and public/private keys.
These types of threats include:
Direct insider threats posed by employees with malicious intent. An employee may accept money from a ransomware group to deploy ransomware directly using their credentials; or the employee may themselves aim to steal information or trade secrets.
Indirect insider threats that originate through third-party business relationships (e.g., supply chain partnerships) or employee incompetence resulting in providing unwitting access to enterprise systems.
Disinformation such as the injection of misinformation into public discourse (e.g., via social media) to damage a company’s reputation or manipulate markets.
User errors leading to system failure and data loss or exfiltration.
Evolve from vulnerability management to continuous threat exposure management
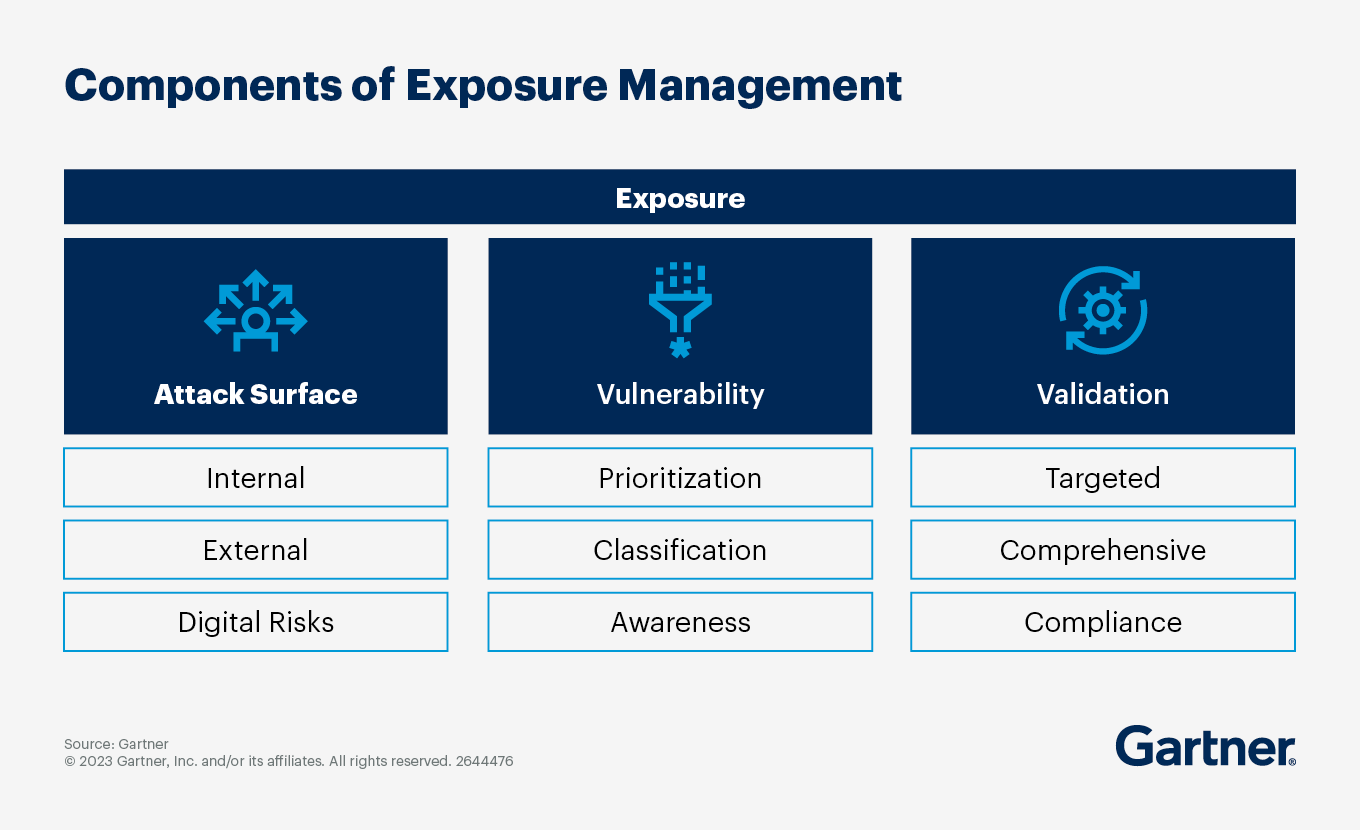
Mitigating against cybersecurity threats is not just about prioritizing which threats to prepare for. It’s also about pursuing a threat management approach that acknowledges the growing attack surface across the organization’s on-premises and cloud resources. Gartner predicts that through 2026, nonpatchable attack surfaces will grow to include more than half of the enterprise. Traditional vulnerability management programs cannot keep up with that growth.
Security and risk teams are instead embracing continuous threat exposure management (CTEM), an integrated, iterative approach to prioritizing and continually refining security posture improvements. The objective of CTEM is to get a consistent, actionable security plan that business executives can understand and architecture teams can act upon.
A CTEM program is governed by five core stages:
Scoping
The attack surface encompasses an extended set of assets, from traditional devices, apps and applications, to less tangible elements such as corporate social media accounts, online code repositories and integrated supply chain systems.
To define the scope of the CTEM initiative, start by understanding what is important to business counterparts, and what impacts are likely to be severe enough to warrant remedial effort. Consider:
- External attack surface
- SaaS security posture
- Digital risk protection
- Dark and deep web sources to identify potential threats to critical assets
Discovery
After scoping, begin a process of discovering assets within that scope and their risk profiles. Include cybersecurity threats, misconfiguration of assets and security controls, as well as counterfeit assets or bad responses to a phishing test as part of the discovery of sources of vulnerability.
Prioritization
Many discovery processes uncover vulnerabilities that go beyond the initial scope. The prioritization step helps cut out the noise.
As with the threats discussed above, prioritizing for the continuous threat exposure management program should be based on the urgency, severity, ability to remediate and level of risk posed to the organization. Using a systematic prioritization method allows the team to clearly articulate which business-critical systems it will prioritize.
Validation
Validation uses controlled simulation or emulation of an attack to understand how malicious actors could execute on cybersecurity threats. The validation step can rely on manual assessment activities, such as red team or penetration testing exercises. It can also leverage automated assessments such as breach and attack simulations. In a CTEM context, validation also assesses suggested remediation approaches for their efficacy and organizational feasibility.
Mobilization
Remediation cannot be fully automated, in part because there is no single fix for any given attack but also because the ultimate decision about how to remediate lies in part with the affected areas of the business. The objective of the “mobilization” effort, therefore, is to reduce friction in the approvals for treatments. It invites organizations to define communication standards and document cross-team approval workflows.
Through 2025, security leaders who implement cross-team mobilization as part of their exposure management program will gain 50% more security optimization than those only prioritizing automated remediation.
Experience IT Security and Risk Management conferences
Join your peers for the unveiling of the latest insights at Gartner conferences.